With cloud adoption skyrocketing, organizations are increasingly turning to multi-cloud strategies, leveraging services from Azure, AWS, and Google Cloud to optimize performance, cost, and flexibility. However, this shift introduces a new challenge—security consistency across multiple cloud platforms. Misconfigurations, identity access issues, and compliance gaps create potential vulnerabilities that cybercriminals actively exploit.
According to Gartner, misconfigurations will cause 99% of cloud security failures through 2025. Organizations need a proactive approach to identify, analyze, and remediate these security risks before they become major incidents. This is where Cloud Security Posture Management (CSPM) becomes a crucial security strategy.
Why is Cloud Security Posture Management Essential in a Multi-Cloud World?
Managing security across different cloud environments is like trying to enforce a single security standard across multiple countries—each with its own rules, processes, and risks. Multi-cloud security requires visibility, automation, and real-time compliance enforcement, which traditional security tools often lack.
Key Challenges Without CSPM:
❌ Lack of Visibility – Security teams struggle to track assets, configurations, and security gaps across multiple cloud environments.
❌ Misconfigurations – Cloud services are misconfigured by default, exposing data to the public or allowing excessive privileges.
❌ Inconsistent Compliance – Regulatory standards like HIPAA, PCI-DSS, GDPR, and ISO 27001 require ongoing compliance, which is difficult across multiple clouds.
❌ Increased Attack Surface – The more services an organization runs across different clouds, the higher the risk of cyberattacks.
How CSPM Addresses These Challenges:
🔹 Real-Time Security Monitoring – CSPM continuously scans cloud configurations, flagging security risks before they escalate.
🔹 Automated Misconfiguration Detection – CSPM tools identify publicly exposed storage, excessive user permissions, and weak authentication settings.
🔹 Continuous Compliance Management – Organizations can automatically map security policies to compliance frameworks and generate audit reports.
🔹 Risk-Based Prioritization – Instead of drowning in alerts, CSPM helps prioritize the most critical risks that attackers could exploit.
Without CSPM, organizations are left guessing whether their cloud environments are secure. With CSPM, security teams can proactively strengthen their cloud defenses and prevent breaches before they happen.
How Microsoft Defender for Cloud Simplifies CSPM
One of the most powerful CSPM solutions in the market is Microsoft Defender for Cloud, which offers multi-cloud security monitoring, compliance tracking, and risk prioritization.
Defender for Cloud CSPM Plans:
| Plan | Features | Cost |
|---|---|---|
| Foundational CSPM (Free) | Baseline security recommendations, compliance tracking, and visibility into misconfigurations. | Free |
| Defender CSPM (Paid) | Advanced AI-driven risk analysis, attack path detection, misconfiguration auto-remediation, and risk prioritization. | Paid (Based on usage) |
- Multi-Cloud Security Management – Monitor and protect workloads across Azure, AWS, and Google Cloud from a single dashboard.
- AI-Driven Risk Prioritization – Uses Microsoft’s threat intelligence to highlight the most critical security risks.
- Attack Path Analysis – Identifies potential attack vectors cybercriminals could exploit to breach cloud environments.
- Compliance Automation – Automatically aligns cloud configurations with NIST, CIS, PCI-DSS, and HIPAA standards.
- Secure Score Visibility – Provides a security score that helps teams track and improve their overall cloud security posture.
Best Practices for Securing Multi-Cloud Environments with CSPM
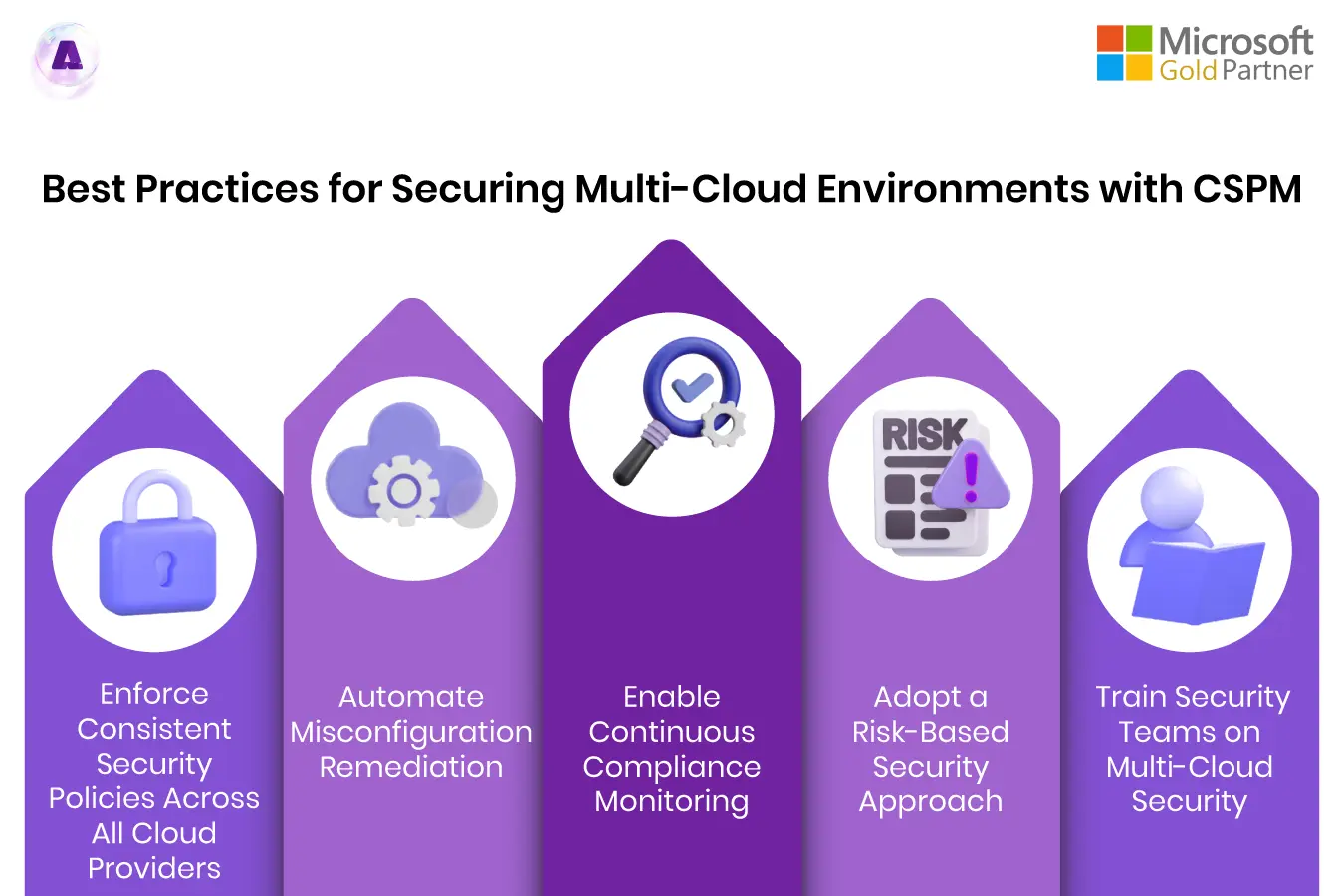
To maximize cloud security and reduce risks, organizations should follow these best practices when using CSPM solutions:
1️⃣ Enforce Consistent Security Policies Across All Cloud Providers:
Standardize security configurations across Azure, AWS, and GCP to prevent inconsistencies.
Use CSPM templates to apply unified security settings across different cloud services.
2️⃣ Automate Misconfiguration Remediation:
Use CSPM tools that auto-correct misconfigurations (e.g., disabling public access to storage).
Integrate Security Orchestration, Automation, and Response (SOAR) for rapid incident response.
3️⃣ Enable Continuous Compliance Monitoring:
Set up real-time compliance tracking to align with CIS Benchmarks, PCI-DSS, and HIPAA.
Generate compliance reports automatically for audit readiness.
4️⃣ Adopt a Risk-Based Security Approach:
Not all security alerts are urgent—focus on high-risk attack vectors first.
Use AI-driven risk analysis (like Microsoft Defender for Cloud) to prioritize threats.
5️⃣ Train Security Teams on Multi-Cloud Security:
Ensure security personnel understand the differences in Azure, AWS, and GCP security models.
Regularly update teams on emerging cloud threats and best practices.



